A cybersecurity firm claims a well-liked Android display recording application that racked up tens of thousands of downloads on Google’s app retail store subsequently commenced spying on its consumers, such as by thieving microphone recordings and other paperwork from the user’s cell phone.
Study by ESET located that the Android application, “iRecorder — Monitor Recorder,” released the destructive code as an app update virtually a calendar year just after it was very first shown on Google Participate in. The code, according to ESET, allowed the application to stealthily upload a moment of ambient audio from the device’s microphone each and every 15 minutes, as well as exfiltrate documents, website internet pages and media files from the user’s cellular phone.
The application is no for a longer time stated in Google Enjoy. If you have put in the application, you should delete it from your gadget. By the time the malicious application was pulled from the app retail store, it had racked up a lot more than 50,000 downloads.
ESET is calling the malicious code AhRat, a personalized version of an open-resource remote entry trojan named AhMyth. Remote entry trojans (or RATs) just take benefit of broad obtain to a victim’s unit and can usually contain remote manage, but also function similarly to spyware and stalkerware.
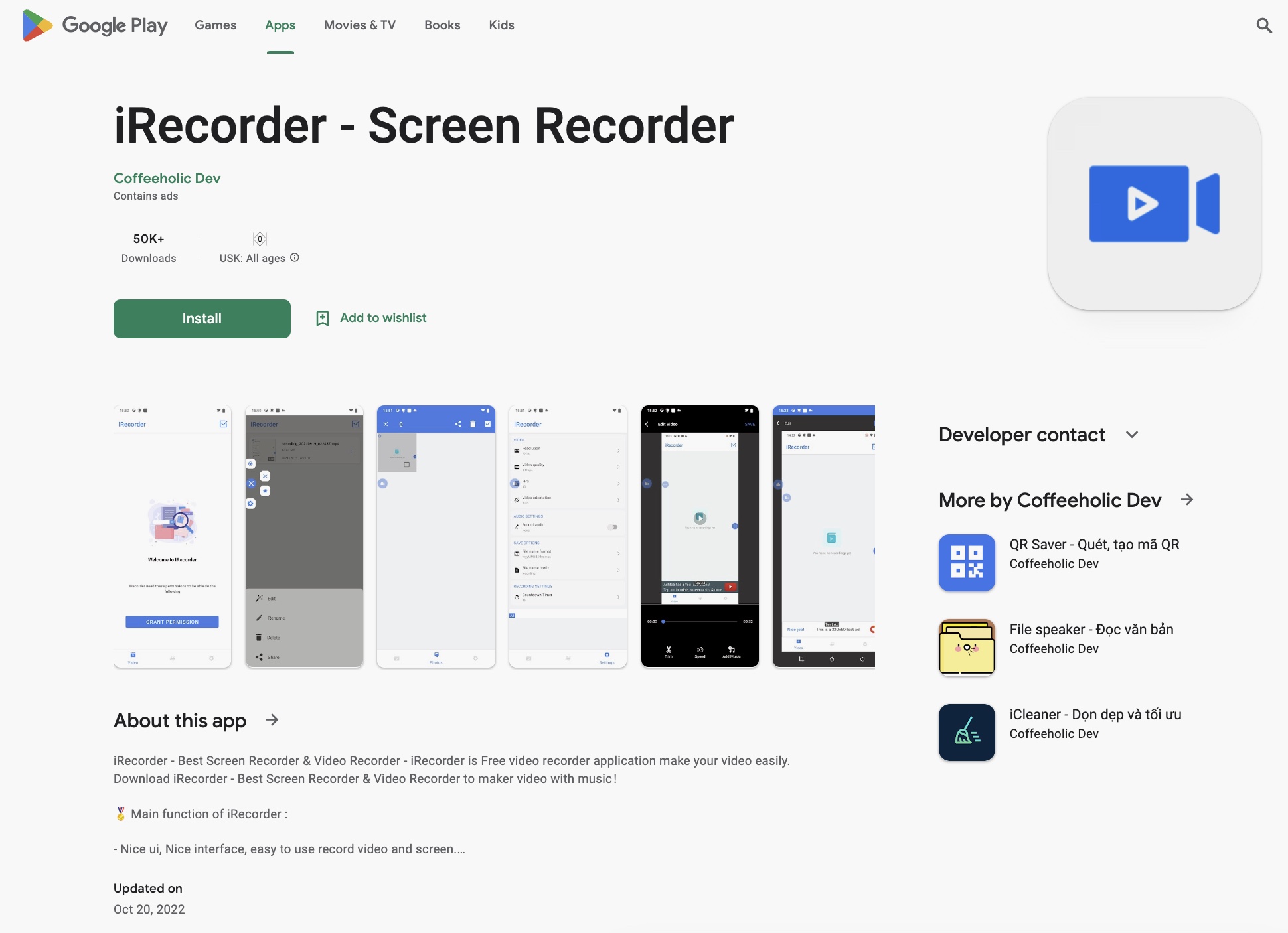
A screenshot of iRecorder stated in Google Enjoy as it was cached in the Online Archive in 2022. Graphic Credits: TechCrunch (screenshot)
Lukas Stefanko, a security researcher at ESET who found the malware, mentioned in a blog submit that the iRecorder application contained no malicious functions when it first released in September 2021.
When the malicious AhRat code was pushed as an app update to present customers (and new people who would down load the application instantly from Google Engage in), the application began stealthily accessing the user’s microphone and uploading the user’s phone facts to a server managed by the malware’s operator. Stefanko mentioned that the audio recording “fit in the now defined application permissions model,” offered that the application was by nature made to capture the device’s display recordings and would request to be granted accessibility to the device’s microphone.
It is not distinct who planted the destructive code — whether the developer or by somebody else — or for what cause. TechCrunch emailed the developer’s e-mail address that was on the app’s listing in advance of it was pulled, but has not yet heard again.
Stefanko stated the destructive code is possible element of a wider espionage campaign — where by hackers operate to gather data on targets of their deciding on — occasionally on behalf of governments or for economically determined explanations. He claimed it was “rare for a developer to upload a legit app, hold out almost a calendar year, and then update it with malicious code.”
It’s not uncommon for terrible apps to slip into the app suppliers, nor is it the 1st time AhMyth has crept its way into Google Engage in. The two Google and Apple display screen apps for malware just before listing them for obtain, and often act proactively to pull applications when they might place buyers at chance. Very last year, Google said it prevented a lot more than 1.4 million privateness-violating applications from achieving Google Enjoy.